There has been, again, some development within the loki domain. Today I’m going to write about the latest module added to the suite, a module for decoding and cracking Cisco’s TACACS+.
TACACS is the Terminal Access Controller Access-Control System, a protocol for handling remote user authentication and central access control. It originated in 1984 and was used in the old Unix world. TACACS+ is a related protocol developed by Cisco Systems and is widely used for AAA (Authentication, Authorization, Accounting) on IOS based devices. It was released as an open standard in 1993 (and expired in 1998 by the way ;-)).
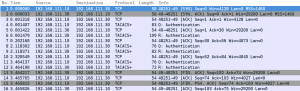
A typical protocol flow can be seen in the screen shot below.
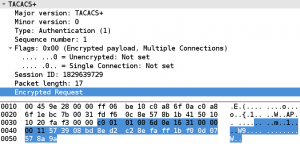
The protocol is build around a common header, containing a version number, a type field, a sequence number, a session id and some flags. The actual protocol payload, which contains the AAA data such as the user name which should be authenticated or the password provided is encrypted. The content of a packets payload can be seen in the next screen shot. The encrypted part of the packet is highlighted.
The encryption is based on a shared secret. A pseudo_pad is generated by concatenating a series of MD5 sums:
pseudo_pad = {MD5_1 [,MD5_2 [ ... ,MD5_n]]}
The MD5 sums are calculated using the session id, the shared secret, the version number, the sequence number and the previous MD5 sum:
MD5_1 = MD5{session_id, key, version, seq_no}
MD5_2 = MD5{session_id, key, version, seq_no, MD5_1}
....
MD5_n = MD5{session_id, key, version, seq_no, MD5_n-1}
The packet payload is then XORed with this pseudo_pad.
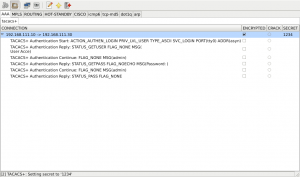
The encryption mechanism and the absence of any kind of checksum makes brute force attempts a bit complicated because we have nothing to (easily) check if we got the right secret. I tried to get around this problem by doing some plausibility checks on the decrypted data such as is the embedded status field in a valid range, are the flags valid and does the payload length match (see tacacs.c:92). That works well most of the time, but under some circumstances the check may produce false positives. I’ll try to enhance the plausibility checks in the future (any ideas are welcome ;-)). After the secret is found, the TACACS+ data can be decrypted and shown, as can be seen in the next screen shot:
As you can see, loki decrypted a (successful) authentication request, the user name is ‘admin’ and the supplied password is also ‘admin’.
The module can be found in the loki svn and is also included in the latest nightly builds. A sample TACACS+ trace can be found here, check it out, test the module and have a nice day!
cheers
/daniel