Internal workshops are one of the reoccurring events at ERNW, that help us to gain knowledge in areas outside our usual expertise. One of the recent workshops which happened during the week from August 22nd-25th was Hardware Hacking. Held by Brian Butterly (@BadgeWizard) and Dominic Spill (@dominicgs), this workshop took place in two parts. Brian kickstarted the introductory session by guiding us through the fundamental steps of Hardware Hacking. Brian did an excellent job of making things simpler by giving a detailed explanation on the basic concepts. For a beginner in hardware hacking, the topic could be rather intimidating if not handled properly.
We began by refreshing our knowledge about the principles of electrical engineering, over information gathering. We became familiarized with the relevant components on circuit boards, identifying their purpose and features, including the rebuilding of the board layouts with CAD tools. Aside from the more theoretical aspects, we also got lots of opportunities for actual hands-on experience.
Starting from high school level knowledge, like playing with a multimeter and capacitors, we began breaking a safe (a physical safe with a digital number lock) and reverse engineering VICTor, an Arduino shield designed by ERNW, for learning purposes. There are a bunch of tools that we became familiarized with during the first two days. This includes both hardware tools like logic analysers, Arduino boards, multimeters and JTAGs, and many software tools like PulseView, minicom and the Arduino IDE. We also worked with interfaces like SPI and I2C. Among all the activities, breaking the safe was the most fun part. The original logic of the safe was replaced by an Arduino with custom firmware, emulating real-life vulnerabilities already found in existing hotel safes. The locking mechanism of the safe required us to enter a 4-digit pin to unlock. The goal was to unlock the safe without any prior knowledge of the actual pin number. One of the techniques we explored to open the safe was based on a timing attack against the locking mechanism. We found out while studying the responses of the lock with the logic analyser attached, that there was a delay in the response graph depending on what digits we pressed. This finding allowed us to eventually bruteforce the correct pin and open the safe.
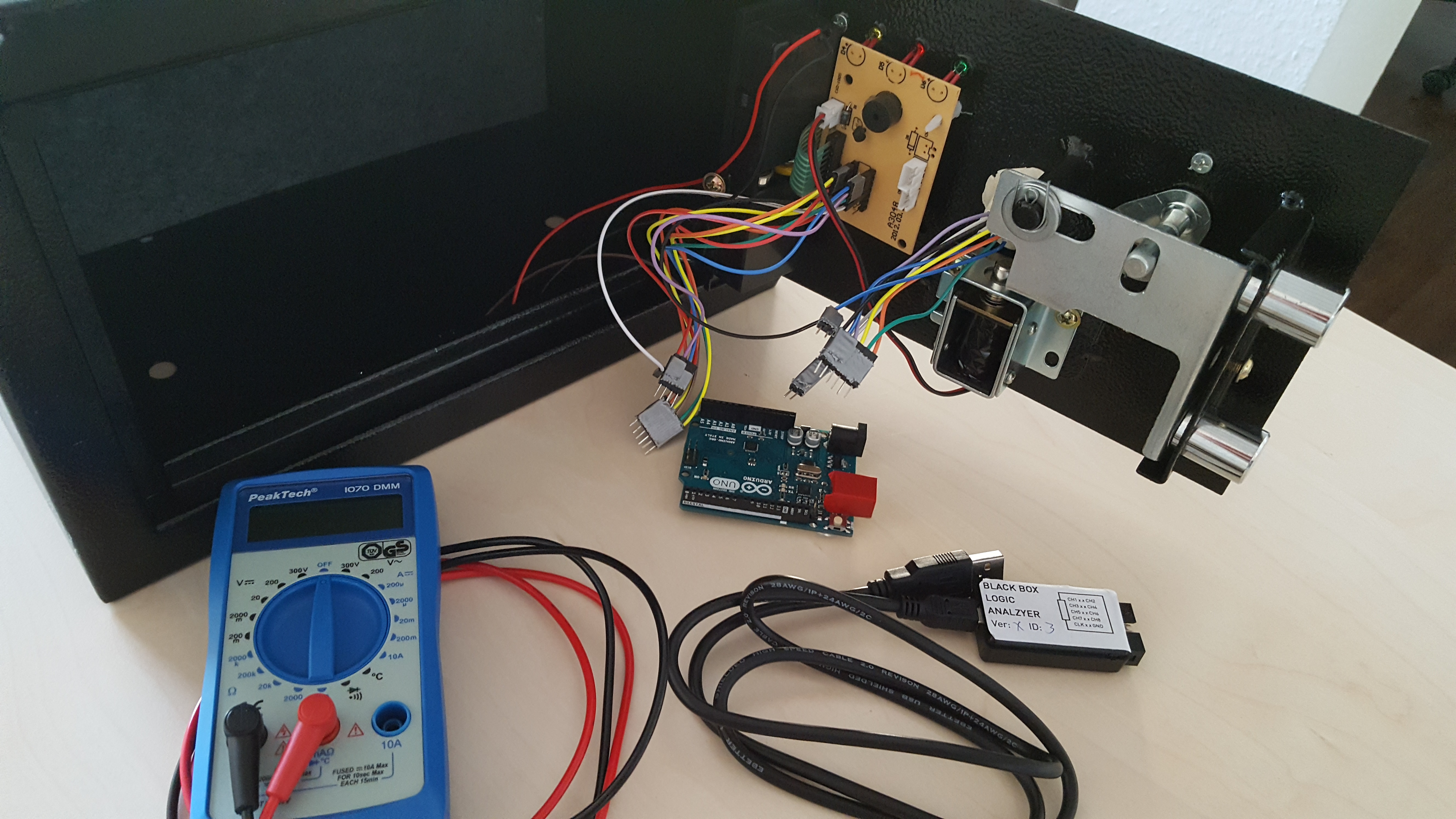
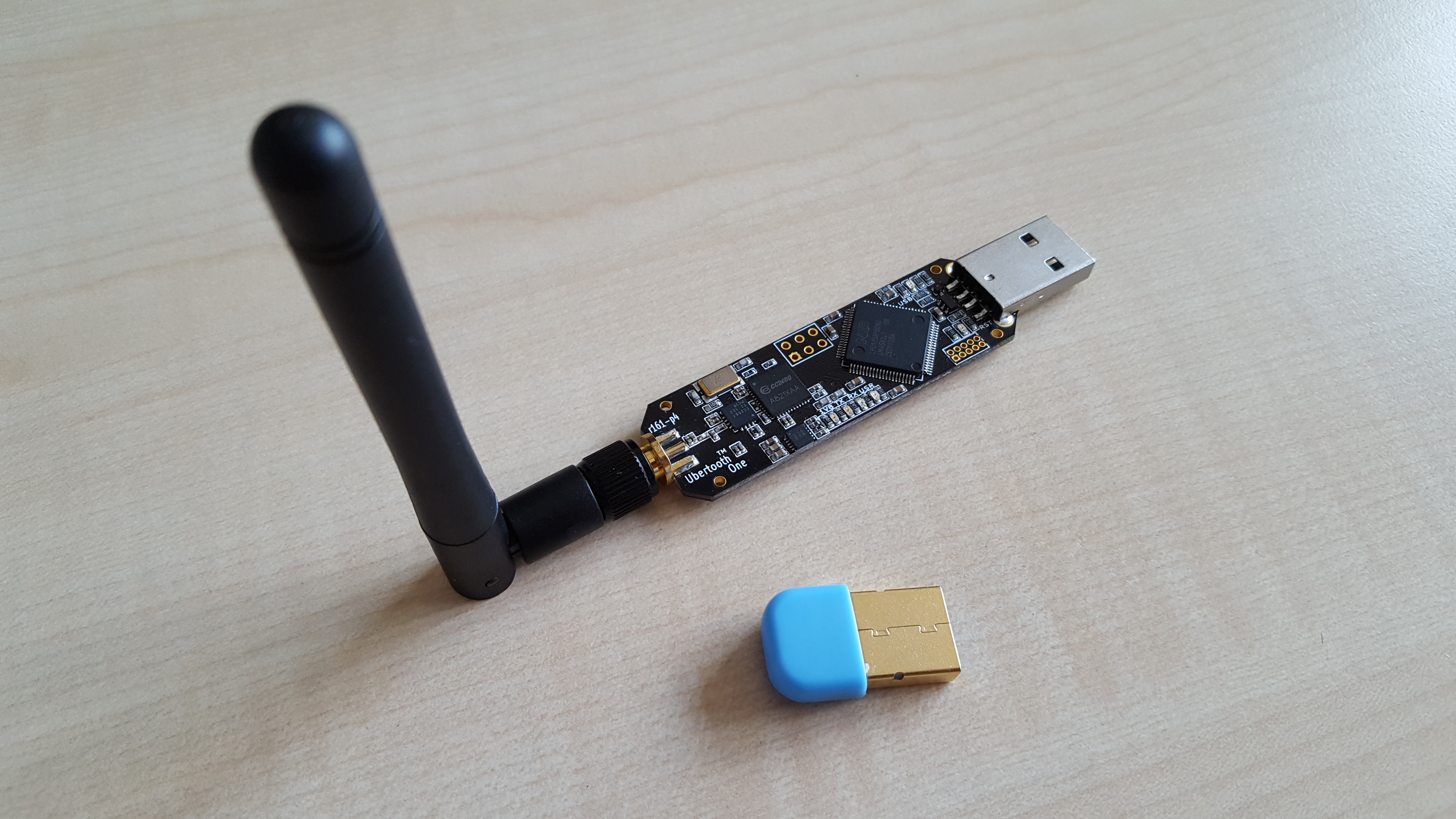
The two days of Hardware Hacking fundamentals were followed by Dominic Spills’ awesome introduction into Bluetooth hacking. Armed with our laptops, a Bluetooth USB dongle and an Ubertooth board, as well as several Bluetooth enabled gadgets in the room, we began our adventures into discovering the capabilities and insecurities of the Bluetooth standard.
We realized pretty quickly that Bluetooth is not necessarily very reliable. Different dongles gave different results in terms of which devices were detected. This caused a good amount of initial irritation.
We started our journey by installing and exploring the basic tools (BlueZ) available on most Linux OSes to interact with Bluetooth hardware. Meanwhile, Dominic explained the history and general capabilities of the Bluetooth standard. Regular Bluetooth devices like our USB-dongles do not provide any means to physically scan for devices that are hidden as per Bluetooth standard. Therefore, we used the Ubertooth which is an open source USB-connectable ARM board with Bluetooth chip and dedicated antenna. Thanks to lots of hands-on exercises and experimentation, we got a pretty good impression of various communications and interactions between the Bluetooth devices. We learned about how to discover services provided by Bluetooth gadgets, to eavesdrop on Bluetooth traffic, record it with known tools like Wireshark or even to spoof other devices to exploit user trust.
The following day we continued the journey where we left off before, this time we focused on Bluetooth Low Energy (BLE) devices. BLE still operates on the same 2.4 GHz band as regular Bluetooth. And once again we had some struggle as some of the dongles, even though seemingly the same model, were apparently BLE capable while others weren’t. Nonetheless, we were able to work around those issues with Dominic’s help and learned about the slight differences in exploring BLE contrary to using regular Bluetooth.
The four days of the workshop went by very quickly, which says a lot about how much fun we had diving into these new topics. The amount of practical experience we gained from using all the different tools and hardware made it, especially, a very worthwhile journey. We are looking forward for yet another hardware hacking workshop to get our hands dirty.
Cheers
Priya & Florian