Last month the annual USENIX Security Symposium with its co-located workshops (WOOT, CSET, FOCI, ASE, and HotSec) was held in Austin, Texas. The program of the conference together with the published papers can be found here and information on the workshops can be found here.
The research topics were quite diverse and included subjects such as low-level attacks, cryptographic attacks, and vehicle attacks. To give you an impression on the research that has been presented at the conference, let us discuss some of the talks in the following:
SoK: XML Parser Vulnerabilities
Christopher Späth, Christian Mainka, Vladislav Mladenov, and Jörg Schwenk, Ruhr University Bochum
This research focused on common and novel vulnerabilities that are present within the XML parsers of widely-used web development programming languages. To perform their research, the authors developed a framework that allows to test for such vulnerabilities in a (partly) automated way. The framework has been published here.
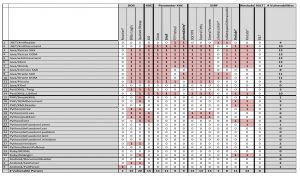
The authors used their framework to test 30 XML parsers in their default configuration for vulnerabilities. The test included all known XML parser vulnerabilities (DOS, XXE, SSRF, XInclude, XSLT). The results of this analysis can be see in the following image, which has been taken from the corresponding research paper (a larger version can be obtained by clicking on the image).
As can be seen from the image, especially Java’s XML parsers (in their default configuration) are vulnerable to the tested attacks (except for KXml). However, certain XML parsers of other programming languages (such as Perl’s XML::LibXml) are also vulnerable to many of the tested attacks. The authors conclude that developers of XML parsers should turn off security critical features by default and only provide an option to enable the feature if needed. Moreover, the risk of enabling such a feature should be sufficiently documented.
The slides and the paper of this talk can be found here.
Truck Hacking: An Experimental Analysis of the SAE J1939 Standard
Yelizaveta Burakova, Bill Hass, Leif Millar, and André Weimerskirch, University of Michigan
This research focused on the security implications originating from the SAE J1939 standard. SAE J1939 standardizes the vehicle bus of heavy vehicles and relies on CAN2.0B for the physical and data link layers. In contrast to consumer vehicles, where the internal network is not standardized, the SAE J1939 is openly available (after a payment has been performed). As a result, implementation details of the internal network of heavy vehicles are readily available. Moreover, potential design flaws of the standard directly affect all vehicles that adhere to the standard.
The researchers analyzed two vehicles that implement the standard: a 2006 Class-8 semi tractor and a 2001 school bus. All attacks have been performed by sending CAN messages via the OBD port of the vehicles. By sending particular CAN messages in this way, the researchers were enable to gain control over the instrument cluster of the tractor (an unmodified attack for the bus, however, did not work).
Moreover, the researchers were able to identify a CAN message for the truck which allowed to control the RPM of the engine. However, in order to gain continuous control, a pause of 40 ms had to be applied within every 7 seconds or else the engine would return to idle. Manual input of the driver via the gas pedal had no effect on the speed while the attack was executed. It has to be noted that the attack also worked without modification on the 2001 school bus. Finally, the identified CAN message for the engine can also be used to disable engine breaking for speeds below 30 miles per hour.
The researchers conclude that since the internal network of many vehicles is based on the SAE J1939 standard, the developed attacks are applicable on a large scale. However, one has to keep in mind that the paper only discusses ‘local’ attacks via the OBD port, i.e. no remote attacks have been discussed. Nevertheless, recent attacks for consumer vehicles (see here or here) indicate that such remote attacks may also be possible for heavy vehicles.
The slides and the paper of this talk can be found here.
A Security Analysis of an In-Vehicle Infotainment and App Platform
Sahar Mazloom, Mohammad Rezaeirad, and Aaron Hunter, George Mason University, New York University
This research focused on security vulnerabilities of an In-Vehicle-Infotainment system (included in at least one 2015 model vehicle) that implements the MirrorLink protocol in order to communicate with the driver’s smart phone. The main question of this research is if an attacker can gain code execution on the In-Vehicle-Infotainment (IVI) system by installing a malicious application on the smart phone (connected to the IVI).
The IVI used by the researchers has been bought via eBay. Initially, MirrorLink was not activated on the IVI, but has been activated later on by updating the IVI with a publicly available (and cryptographically signed) firmware image. Furthermore, one configuration value had to be modified in order to enable the MirrorLink support. It is noted that by unpacking the update image, the researchers also gained access to the main executables that ran on the IVI.
A custom build USB sniffer has been used to capture the network traffic between the smart phone and the IVI unit. An analysis of the traffic showed that the MirrorLink protocol implements several phases. In the first phase, USB-related traffic has been exchanged between the smart phone and the IVI in order to correctly configure the USB interfaces. In a second phase, the smart phone functions as a DHCP server and assigns an IP address to the IVI unit. Finally, UPnP messages are exchanged between the IVI unit and the smart phone. One important detail of this last phase is that the IVI system downloads XML configuration files from the smart phone during this last phase.
By modifying the XML configuration files (which were downloaded by the IVI), it was possible to overflow a buffer located on the heap on the IVI. This overflow allowed the researchers to gain control flow of a privileged process that ran on the IVI.
The authors conclude that by exploiting the found vulnerabilities it may be possible to send malicious messages to the CAN bus of the vehicle via the IVI. However, working Proof-of-Concept code for this assumption has not been disclosed.
The slides and the paper of this talk can be found here.
All talks summarized so far were held during the WOOT workshop. A summary of some of the talks of the main Usenix conference will be provided later on by Brian.
Cheers
Oliver