When it comes to SAP, Troopers has two events that are about Security in SAP Systems in particular. On the first day of the Troopers16 Trainings the BIZEC workshop takes place. The second event is a dedicated SAP track during the conference. Apart from these events there were of course a lot of nice folks to talk to (about SAP) 🙂 This post is a short overview about SAP security @ TROOPERS16.
BIZEC-Workshop
“The Business Application Security Initiative (BIZEC.org) is a non-profit organization with a focus on security defects in business applications.”
The corresponding workshop was split into sessions explaining common problems in SAP landscapes and how to deal with and mitigate them. Researchers from different companies such as Akquinet, ERPSec, ESNC, Onapsis and Virtual Forge were on hand to share their knowledge. There were demonstrations and the attendees could comprehend the vulnerabilities shown during the presentations on their own. This was fun as these challenges were organized in a Capture-the-Flag competition where the attendees had to collect tokens. During these sessions a lot of interesting questions came up that were talked about in a discussion at the end of the day, followed by a shared networking dinner.
Sad to say that there are no recordings, so if you are interested in taking part maybe you should attend the workshop next year 😉
SAP Security Track
In 2014, we introduced something new. A special track covering a dedicated topic on the first conference day – the SAP track. This year it covered topics going from operational issues to low level exploitation of SAP services. The following section is just a brief insight of what happened at TROOPERS. See this LINK to get a complete overview of all the talks.
Joris van de Vis – An unknown SAP default Account
Joris spoke about an unknown SAP default account as described in his guest blog post. During the presentation he spoke about how default accounts are still a risk for today’s SAP systems and why SAP administrators should constantly check for the presence of these default accounts. Furthermore, he showed a tool to check you Solution Manager instances which is free to use. Find the tool HERE and the slides HERE.
https://www.youtube.com/watch?v=Wi79pGsp90c
Martin Gallo – deep dive into SAP archive file formats
Martin Gallo, researcher at Core Security, presented his work on SAP archive file formats. He pointed out the importance of archive file formats, respectively the files which are used for shipping software and features. Until now there were no practical attacks and no public documentation about this.
He gave an overview of the different algorithms used to compress the data/ information and the difference in the version of the compression formats showing the header format. The main difference of the newer version is that the filename string is null terminated. The image shows the representation of the archive file header.
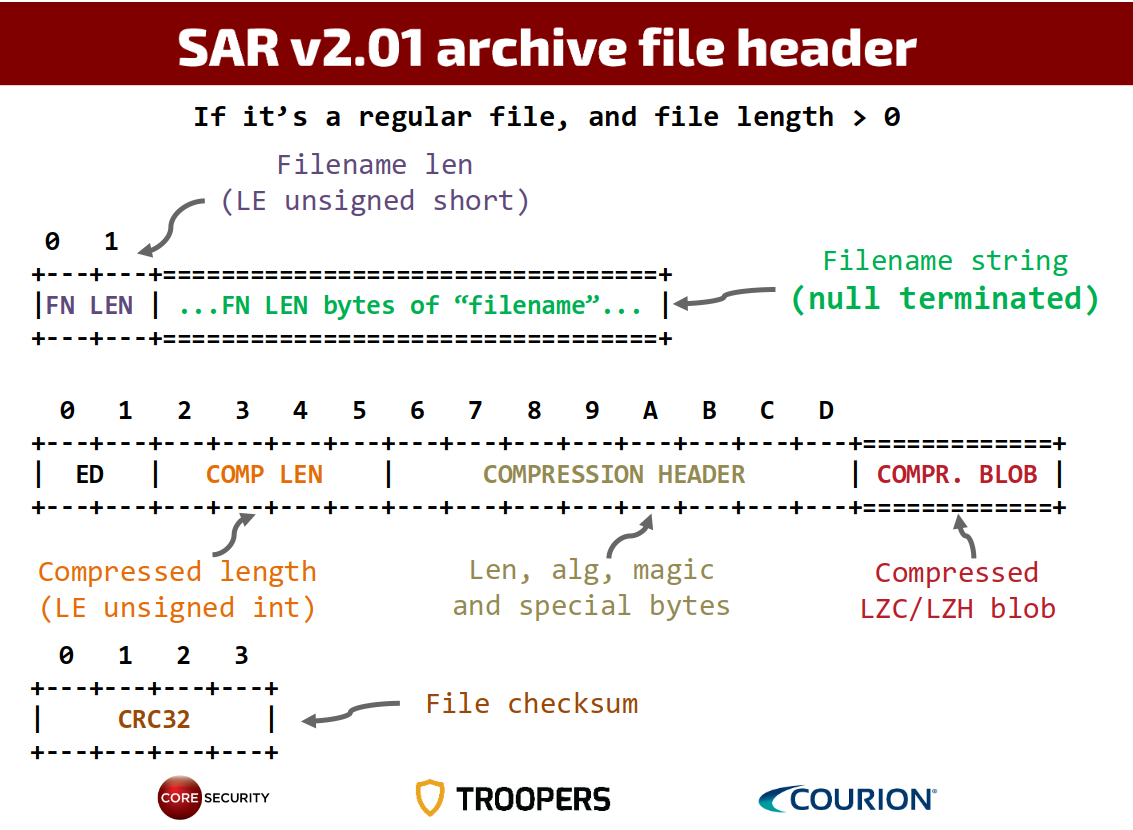
After showing the details of the archive file formats he went on talk about the attack surface that is exposed by these archives. How is the parsing of the data and information in these files handled? The main goal: bypass file signature checks, so an attacker can tamper with files. By using a fuzzing approach he was able to crash the sapcar program used to validate, unpack and create SAP archive files. The compression algorithms used in sapcar are widely used for different SAP components and use the same implementation. Under this circumstance, he was able to identify different types of vulnerabilities – for example Denial of Service attacks – while decompressing data. He added his archive format research results to the python library for RFC called pysap also maintained by Gallo which is definitely worth a look.
“pysap is a Python library that provides modules for crafting and sending packets using SAP’s NI, Message Server, Router, RFC, SNC, Enqueue and Diag protocols. The modules are build on top of Scapy and are based on information acquired at researching the different protocols and services.”
As discussed in the “Patch me if you can” talk an attacker could intercept and inject SAP download traffic. Gallo thought of a scenario where a user downloads something from the SAP market place and an attacker injects/infects files on the fly downloaded from the marketplace. By showing his research about the archive files formats, Martin Gallo unveiled new attack vectors for SAP systems.
https://www.youtube.com/watch?v=TO4-qTTjhp0
Find the slides of the talk: HERE
Have a safe day!