Over the past few weeks, multiple news sites have covered some mystical approach to bruteforce PINs on Apple iOS devices. All articles cover a black box called IP Box, the fact that PINs can be broken and that sometimes the automatic wipe after 10 failed tries can be circumvented. Sadly, as often, the what is described but not the how……
This blog post will give you a simple overview of both the practical attacks and the vulnerabilities behind them. Although the Headings don’t quite give away the content, the post starts with a simple PIN bruteforce against iOS 7.x and then goes over to a more advanced attack on iOS 8.x and a few technical details on the “black box”.
The Black Box
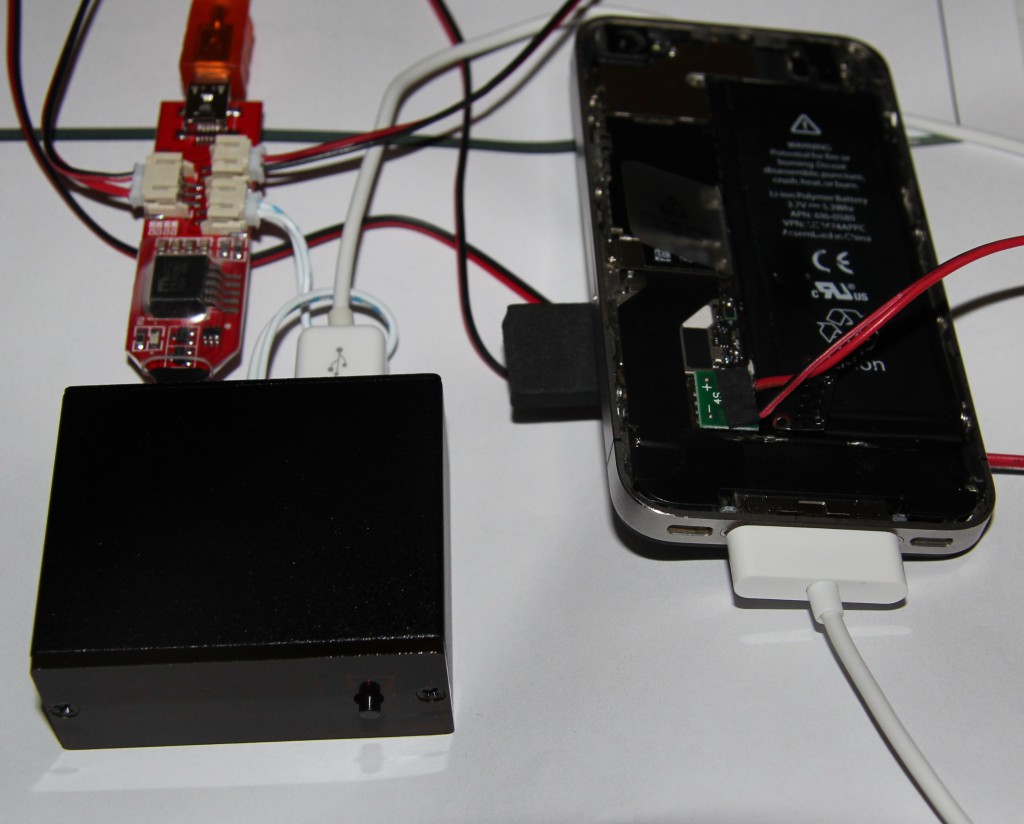
The covered black box is called “IP Box” and can be bought all over the Internet for about 165€ including all wires and connectors. It comes as an actual black box, with a 4 LED display, a push button, a mini-USB and a USB-A socket and a PIN head for a light sensor. The mini-USB socket goes towards the host computer (although it can also go for stand alone mode) and the USB-A socket goes towards the target device (having USB-A means you can use a default iPhone cable).
A quick attack on iOS 7.1.2
We’ll start with an iPhone 4 running iOS 7.1.2 and I’ll skip flashing the device for now.
Connect the black box to the iPhone with a normal iPhone cable, stick the light sensor onto the screen with a bit of tape or Blue-Tack and give it a second. The LEDs will light up and start counting from 0000. The device will vibrate after the first entry, which is the usual reaction for “wrong PIN”. After a few tries the black box starts to beep, the sign for “PIN found”, and states a false positive. The reason for this can be seen on the iPhone screen “please try again in 1 Minutes”, which has triggered the light sensor. The device has run into the cool down time, protecting against bruteforce attacks. Following the instructions, I press the button and it carries on.
Now comes the first finding!
The device still tells me to wait a minute but vibrates on the entry of a PIN!
A while later the black box beeps again and the device is unlocked.
Some Explanations
How does it work? Well, let’s just call it a TROOPERS14 badge. The black box emulates a USB HID device, keyboard, and sends keystrokes to the device. This is quickly confirmed after opening a text editor on the phone and starting the black box.
Above that We’ve just found an iOS vulnerability: The iPhone will accept PIN entries via USB even though the device is locked by the cool down window. Grabbing an Apple keyboard (the cheap ones I had were declined by the iPhone as not being supported) and a powered USB hub (the iPhone said the keyboard drew to much current) the vulnerability can quickly be proven. After bringing the phone into cool down time, I can still enter wrong and also the correct PIN without any problems.
Attacking iOS 8
Sadly I was not able to reach an iOS 8 device <8.2, so this part will partially be based on other reports on the topic and the rest on an iPhone 4S with iOS 8.2.
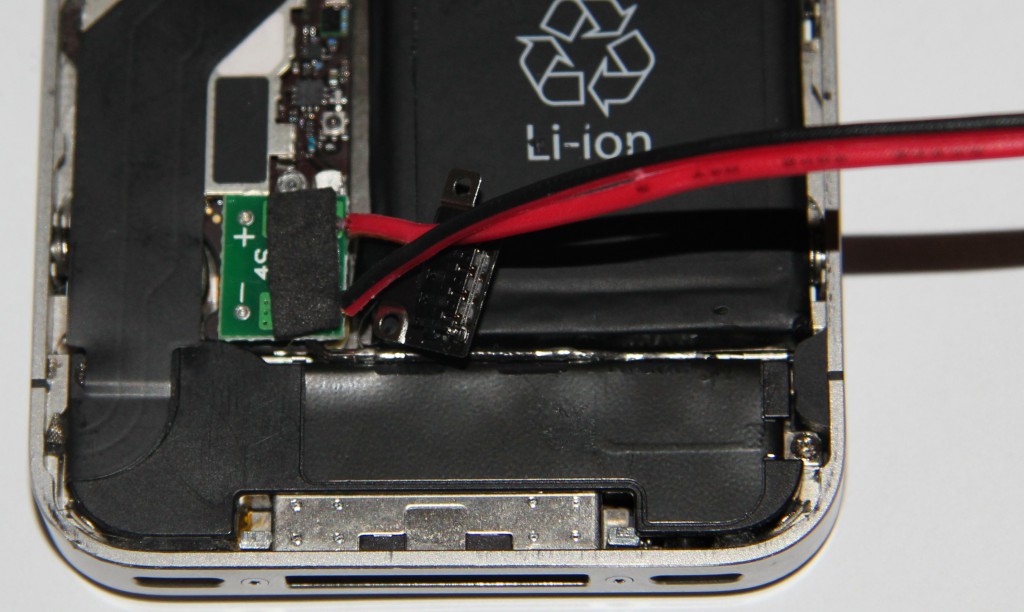
An extra iOS 8 adapter for the IP Box is available on the Internet, which is necessary for the documented attacks. The adapter gets connected to mini-USB and the light sensor socket on the black box. Then the adapter is connected to the battery connector in the iPhone (yes, you do need to open it). Finally the black box is connected to the iPhone via the iPhone cable, the light sensor stuck onto the display and the IP Box is connected to a USB port on the computer.
Now the whole bruteforcing process starts, yet again, with a small difference. Directly after entering the incorrect PIN, the iPhone looses power and restarts. The black box also turns of during the restart progress (see the diagram further down for the reason) and restarts with a static timer, before entering the next PIN.
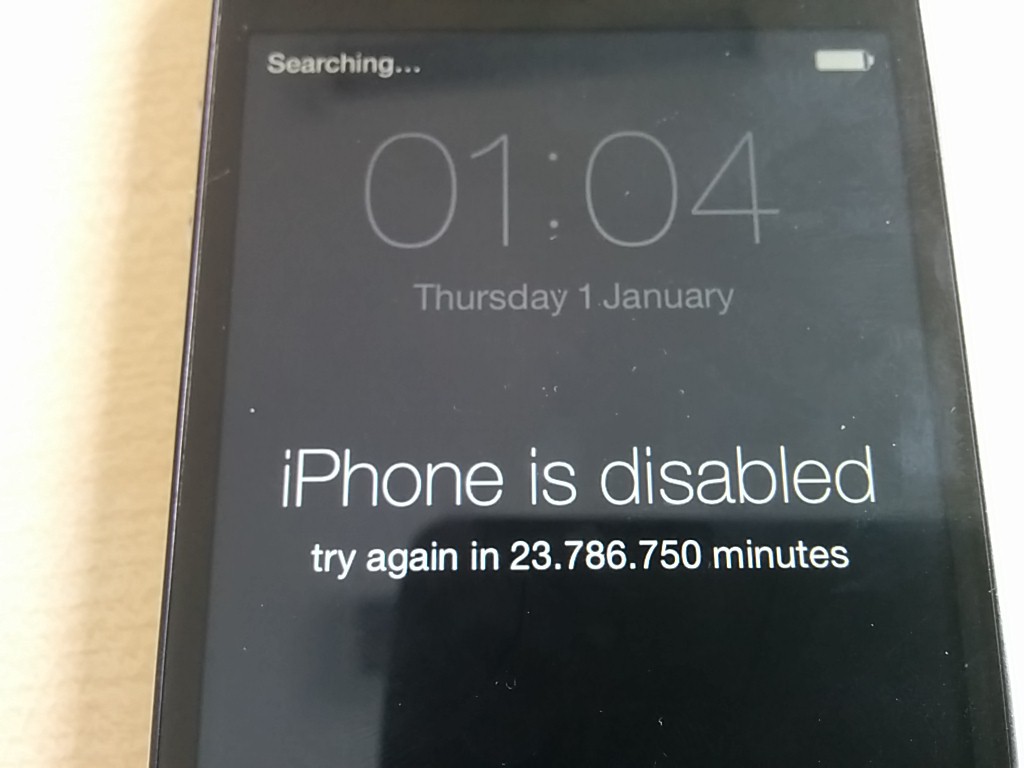
From the various reports it seems that on different iOS 8.1.x versions, iOS does not store the failed entry quick enough. This results in the fact that after restarting the phone, the bruteforce is back to first try. This approach both circumvents the cool down time, and the wipe after 10 incorrect entries.
As said before I was not able to actually verify this attack, except for the fact that it did not work on my iOS 8.2 iPhone 4S. Although the device restarted, it carried on counting the incorrect entries and ran into the cool down time, which on iOS 8.2 is actually effective against USB entries.
The How
The first vulnerability was fixed (the cool down time works) and now there is a second one in use: iOS has an insecure counter for incorrect PIN entries. This type of attack is not new and has been run against smart cards in the past. The idea is that if the device can not increase the wrong PIN counter, one can happily run bruteforce attacks. Yet again, this vulnerability seems to be fixed in iOS 8.2 (one would usually increase the wrong PIN counter before validating the PIN and resetting the counter only if the PIN was correct).
Details, Details, Electronics
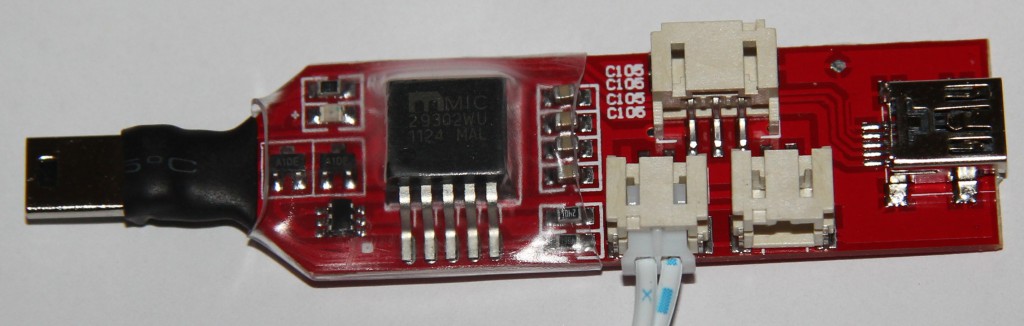
The IP Box itself consists of a single microcontroller, with connections for the display, the light sensor, the target device and a host computer. The box draws its power from the target device, so no computer is needed, but a target device is needed when using the box from a computer. The light sensor is used to identify “state changes”, changes in the brightness level on a selected spot of the screen. So all in all it does a good job, but isn’t really a very sophisticated design.
The iOS 8 adapter consists of a DCDC converter which powers the iPhone and kills it, when it’s switched off, a few resistors and transistors. It’s simply an add-on to make switching the phone off quickly possible.
Flashing the Black Box
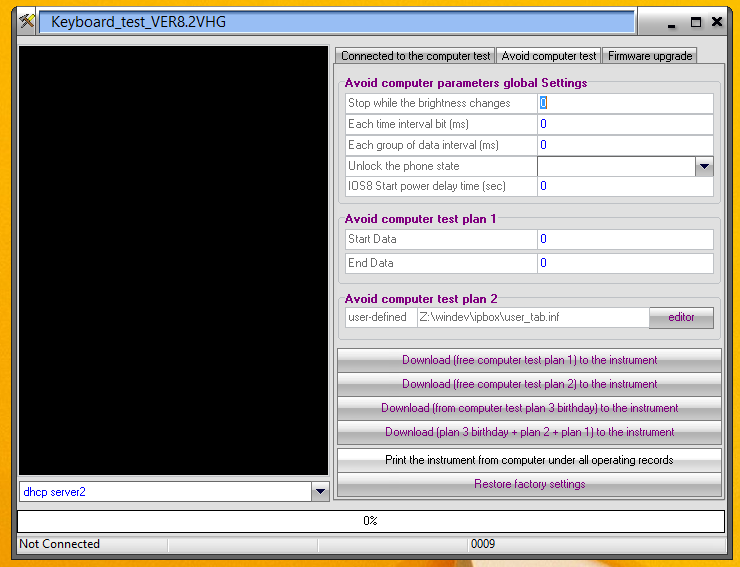
Depending on what exactly you want to do, you need to change the configuration (firmware) on the black box. For this you can get a configuration tool, which made the virus scanner in my victim VM pop up. A quick run through virustotal.com partially confirmed the file to be potentially unwanted. As for all strange tools: never run them in productive VM!
When you connect the black box to the computer via USB nothing will happen, as you need a connected iPhone to power the box! When it’s actually running, it will be detected by the flashing utility and you can push your configuration. For the next test I’ll be going for the iOS 8 firmware and payload.
FurtherFun with the Software
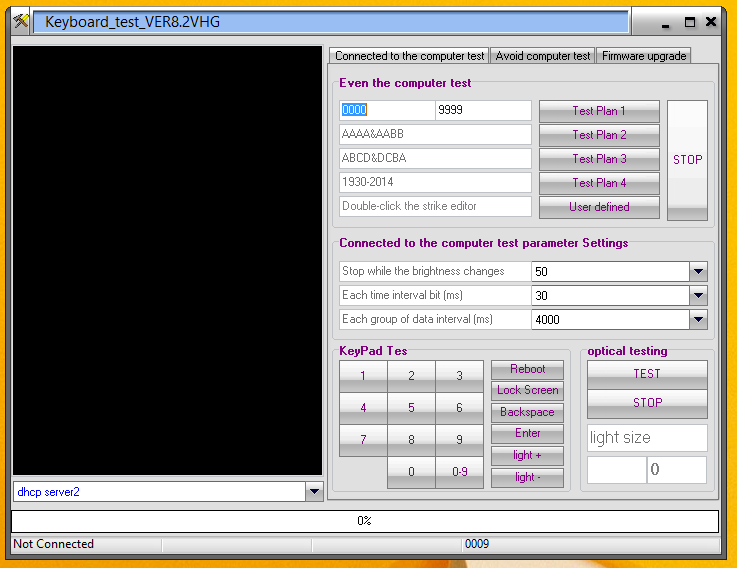
Above being able to flash the black box, the software can also be used to directly remote control the device. The KeyPad area can be used to directly enter digits into the device, without needing an extra keyboard. Alternatively the bruteforce can be run from a PC instead of the firmware.
Mitigations
Mitigations in this case are very simple:
-Don’t use iOS 7.1.2 devices (especially as they’re already deprecated due to various other reasons)
-Don’t use simple 4 digit PINs
-Keep your device up to date
Summary
So it turns out iOS seems to have had two rather ugly vulnerabilities included for quite a while. I guess the possibility to bypass a cool down time screen, simply by using a USB keyboard instead of the unreachable on-screen PIN pad is something for an epic fail compilation. Still, the second vulnerability, entering wrong PINs without increasing the wipe-after-10-wrong-inputs counter is probably even worse, concerning its potential impact on corporate devices.
Luckily Apple seems to have patched both problems in the newest iOS versions, so it’s time for an update.
Above all that, the black box can also be used for simple DoS attacks against an iPhone.
So long,
Brian